Scan Container in Azure Container Registry with Snyk via Azure DevOps Pipeline
Monday, January 23, 2023
Scan Container in Azure Container Registry with Snyk via Azure DevOps Pipeline
#azure-container-registry #azure-devops #containers #devsecops #docker #security-vulnerabilities #snyk
This article is published at GitHub.You can raise issues, create pull requests or even fork the content...its open source.
In this article, you will learn how to scan a container image in Azure Container Registry with Snyk via Azure DevOps Pipelines.
Prerequisites
The following prerequisites will be required to complete this tutorial:
- Azure DevOps account. If you don't have an Azure DevOps account, create one for free before you begin.
- Azure DevOps project, with a code repository that has docker support.
- Azure account. If you don't have an Azure account, create one for free before you begin.
- Snyk account. If you don't have a Snyk account, create one for free before you begin.
Add Snyk Extension to Azure DevOps
In the root of an Azure DevOps Organization, select Organization Settings in the bottom left of the screen.

In the General section, select Extensions.
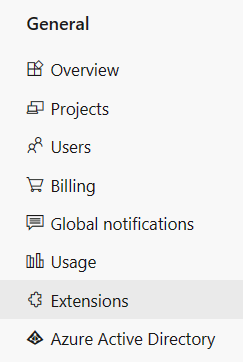
Select Browse marketplace.
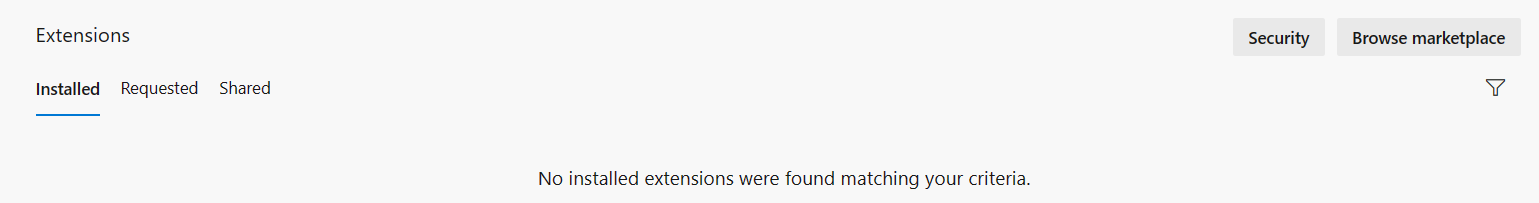
Search for snyk, and then select Snyk Security Scan.
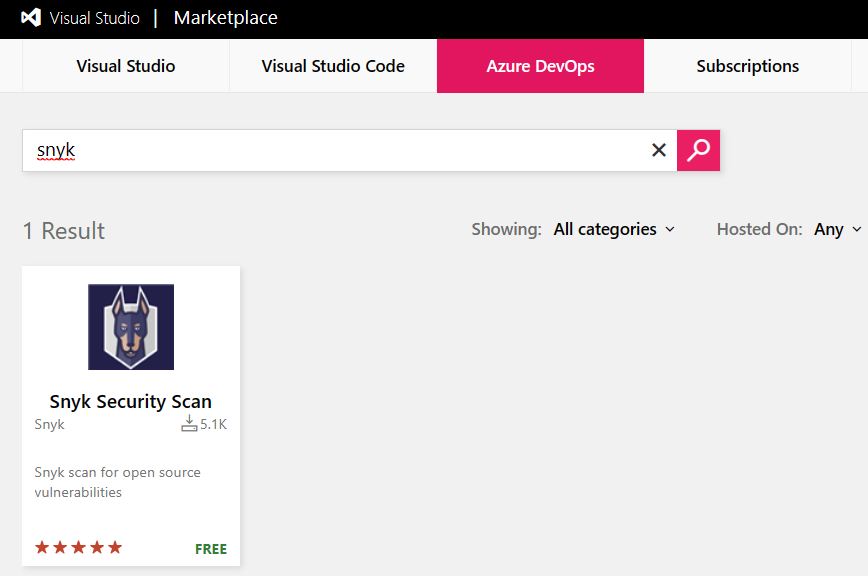
Select Get if free, and then select Install.
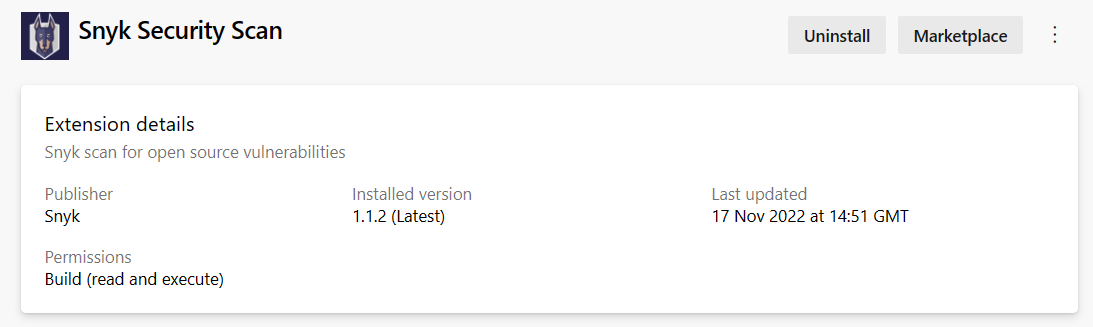
In the Extensions section, Snyk Security Scan is now installed.
Create Azure Container Registry
In Azure Portal, search for container registry.
Select + Create.
Enter the following values in the Basics tab, then select the Review + create tab, and then select Create.
Parameter Value Subscription Your Azure Subscription Resource group Create new with a name of your choice Registry name Chosen name for the registry Location North Europe SKU Basic 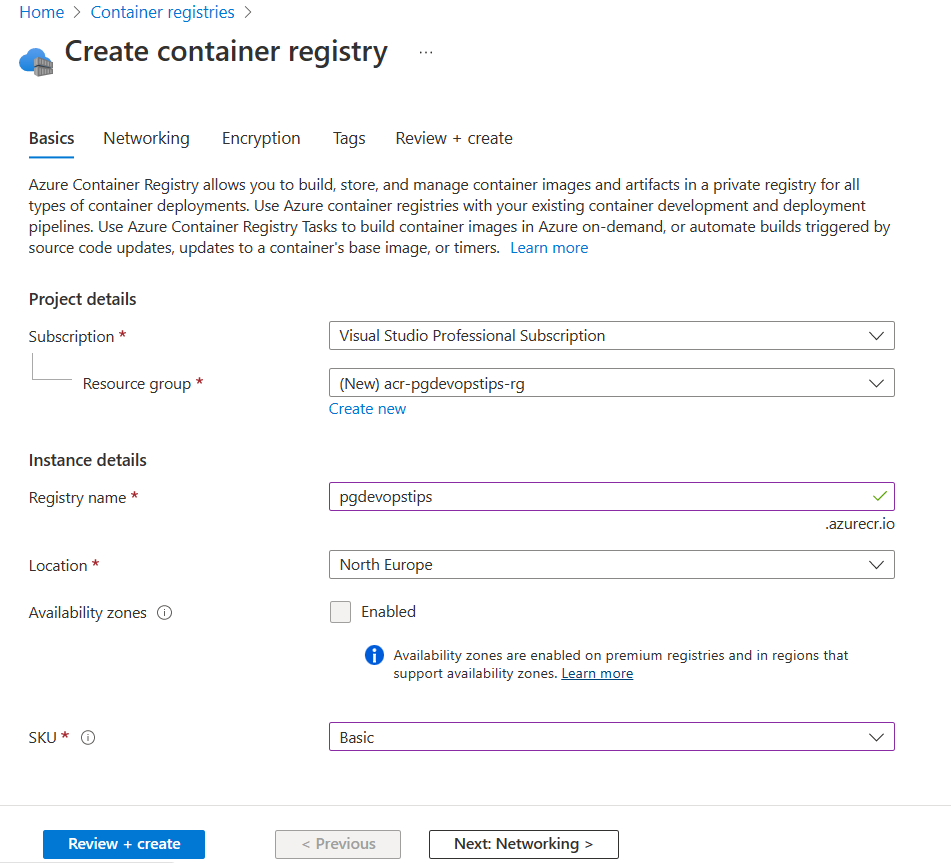
Add Snyk Service Connection to Azure DevOps Project
From the root of an Azure DevOps Project, select Project settings in the bottom left of the screen.
In the Pipelines section, select Service connections.
Select Create service connection.
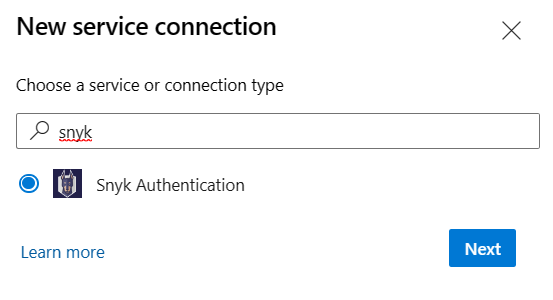
Search for snyk, then select Next.
Enter the following values.
Parameter Value Server URL https://snyk.io/ Snyk API Token Your Snyk API Token (see below) Service connection name Snyk Grant access permission to all pipelines True 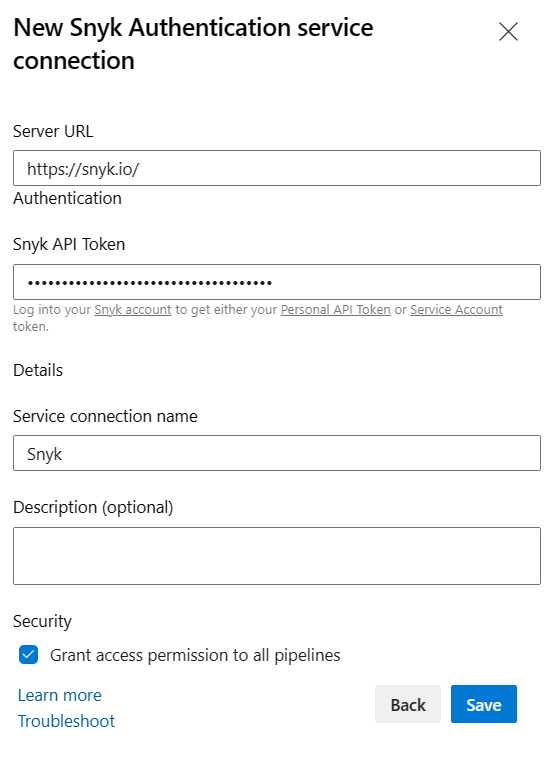
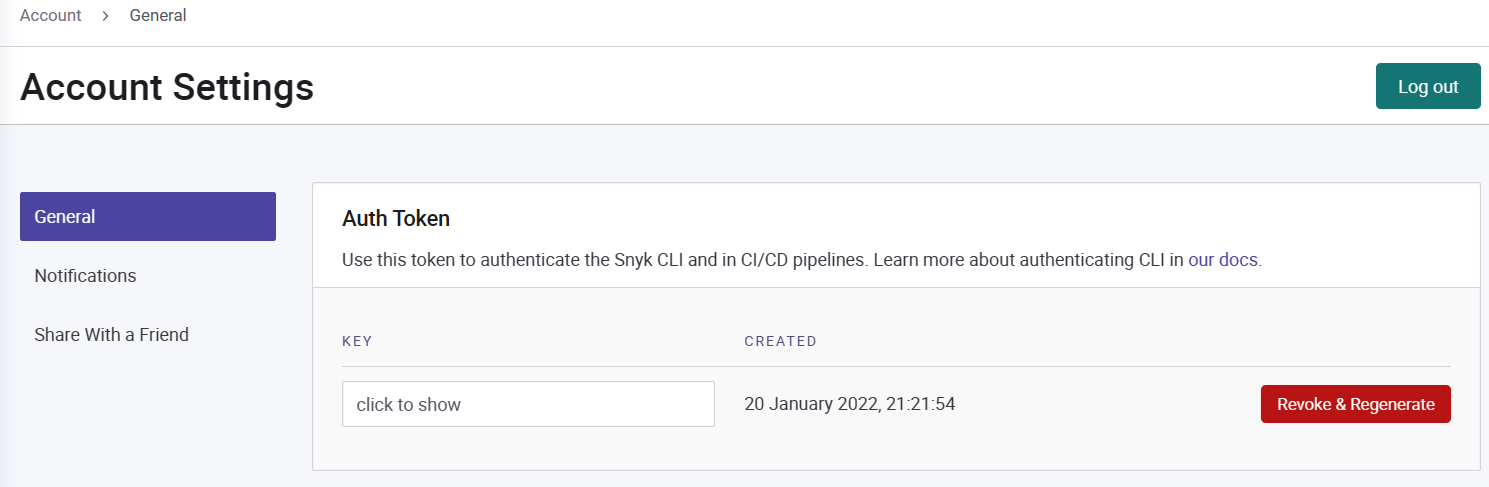
To get the Snyk API Token, in snyk account settings, select General, then select click to show the Key. Copy and paste the key into Azure DevOps Snyk Service Connection Setup Personal API Token box.
Add Azure Container Registry Service Connection to Azure DevOps Project
Complete steps 1 and 2 in Add Snyk Service Connection to Azure DevOps Project.
Select New service connection.

Search for docker, and then select Docker Registry.
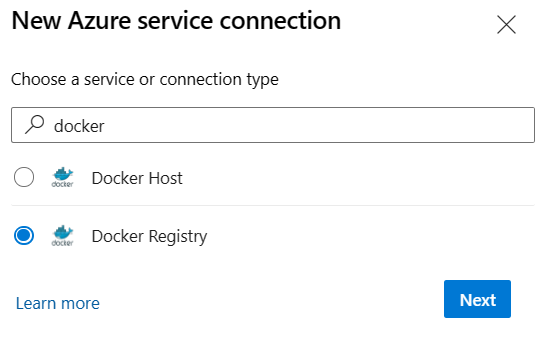
Enter the following values.
Parameter Value Registry type Azure Container Registry Authentication Type Service Principal Subscription Your Azure Subscription Azure container registry Azure Container Registry created earlier Service connection name Chosen name for the service connection Grant access permission to all pipelines True 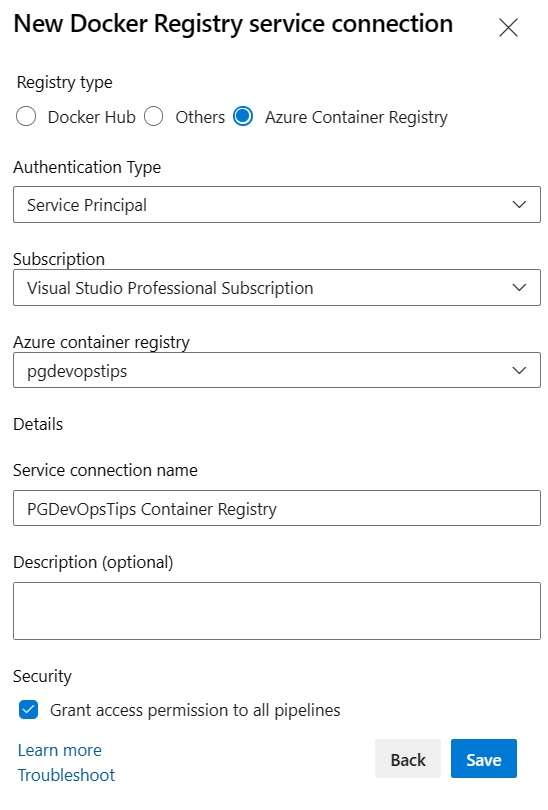
Add Azure DevOps Snyk Pipeline
In the root of an Azure DevOps Project, select Repos.
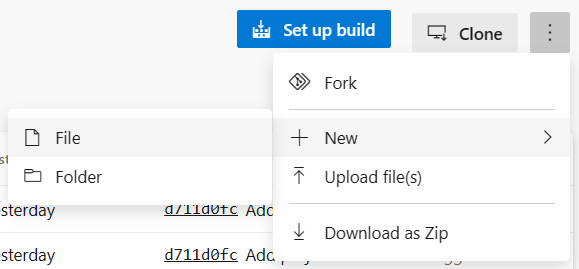
Whilst in the root of your repo, select More actions, then + New, and then File.
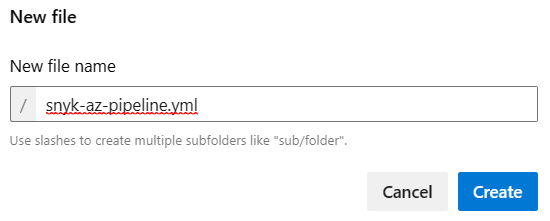
In the Modal Popup, add the file name snyk-az-pipeline.yml into the New file name text box.
Add the following contents to the snyk-az-pipeline.yml file, replacing
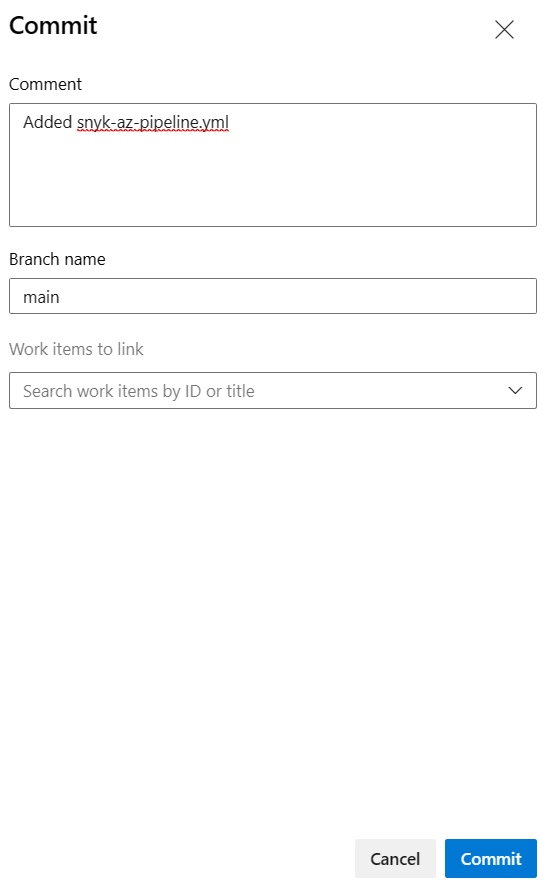
{Your...}with your project folder name, azure container registry, repository and login server url (usually ends in .azurecr.io).trigger: - main pool: vmImage: ubuntu-latest variables: buildConfiguration: 'Release' jobs: - job: Build steps: - task: DotNetCoreCLI@2 continueOnError: false inputs: command: 'build' projects: '{YourProjectFolder}*/**.csproj' - job: Build_and_Push_Docker_Image dependsOn: Build displayName: Build & Deploy to Azure Registry pool: vmImage: ubuntu-latest steps: - checkout: self - task: Docker@2 displayName: Build an image inputs: containerRegistry: '{YourAzureContainerRegistryConnectionSetupAbove}' repository: '{YourNewAzureContainerRegistryRepository}' command: 'build' Dockerfile: '{YourProjectFolder}/Dockerfile' buildContext: '.' tags: 'dev' - task: SnykSecurityScan@1 displayName: Scan an image inputs: serviceConnectionEndpoint: 'Snyk' testType: 'container' dockerImageName: '{YourAzureContainerRegistryLoginServerUrl}/{YourAzureContainerRegistryRepository}:dev' dockerfilePath: '{YourProjectFolder}/Dockerfile' monitorWhen: 'always' failOnIssues: true - task: Docker@2 displayName: Push an image inputs: containerRegistry: '{YourAzureContainerRegistryConnectionSetupAbove}' repository: '{YourNewAzureContainerRegistryRepository}' command: 'push' tags: devIn the top right, select Commit.
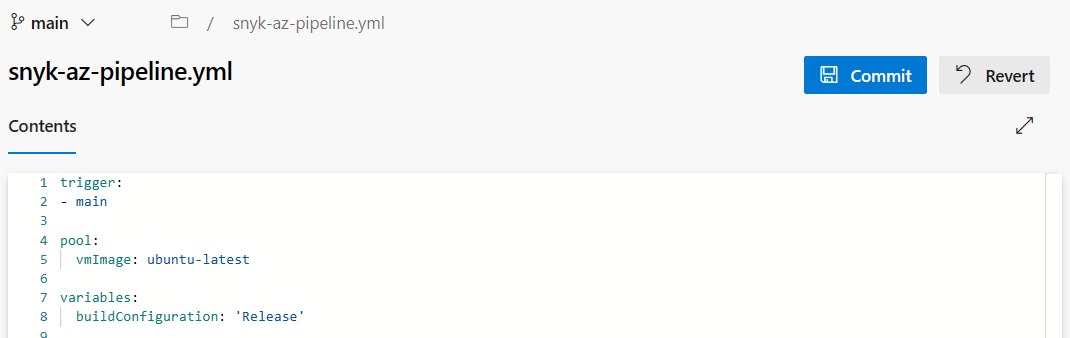
In the bottom right, select Commit.
Create and Run Azure DevOps Snyk Pipeline
From the root of an Azure DevOps Project, select Pipelines.
Select Create Pipeline.
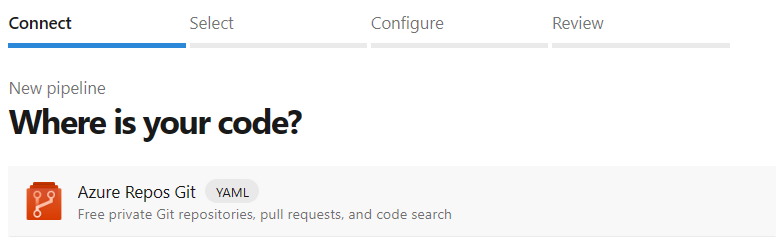
In the Connect tab, Select Azure Repos Git.
In the Select tab, select Existing Azure Pipelines YAML file.
Enter the following values.
Parameter Value Branch main Path /snyk-az-pipeline.yml 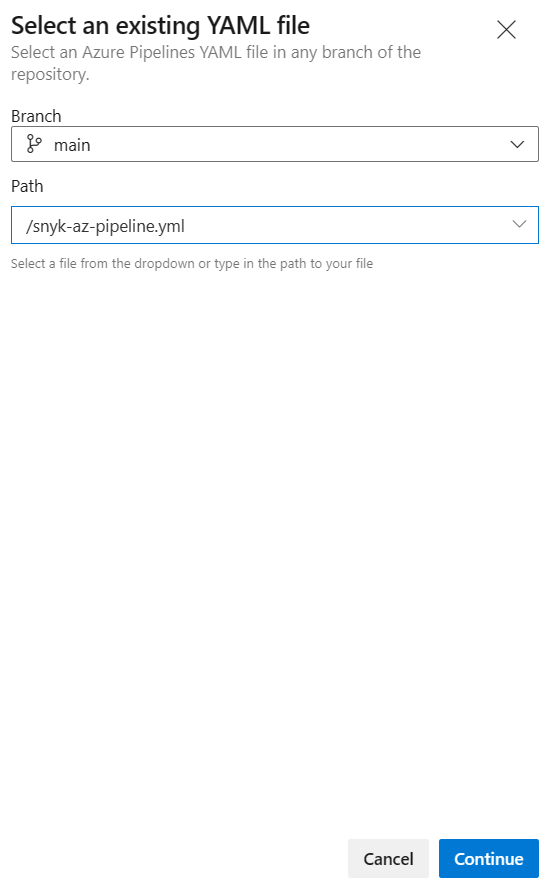
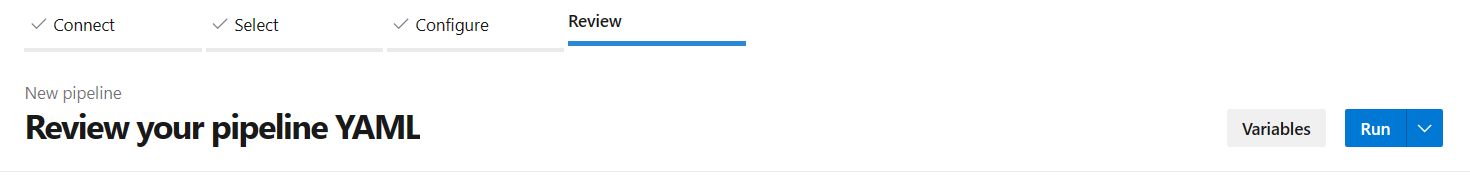
Review the pipeline snyk-az-pipeline.yml yaml, and then select Run, to run the pipeline.
View Snyk Test Report
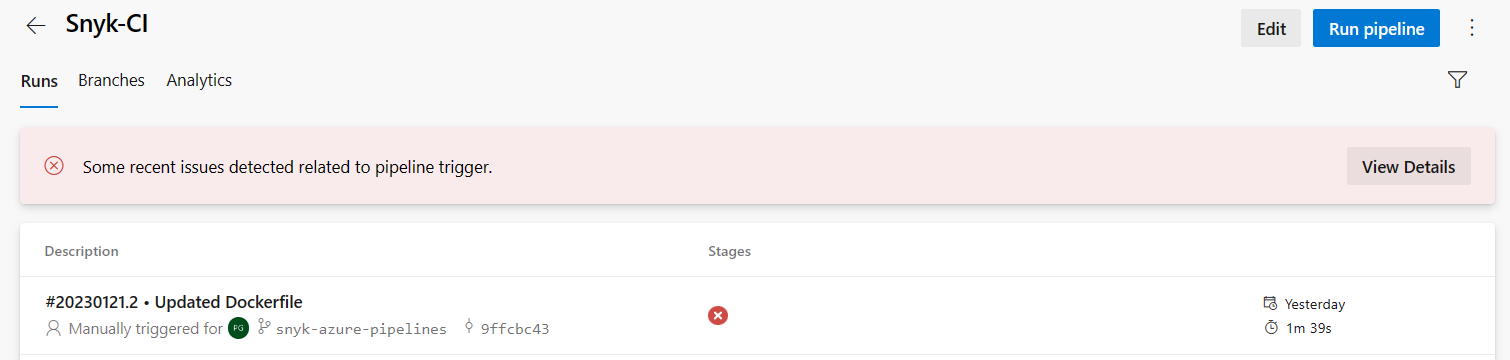
Navigate to Pipelines.
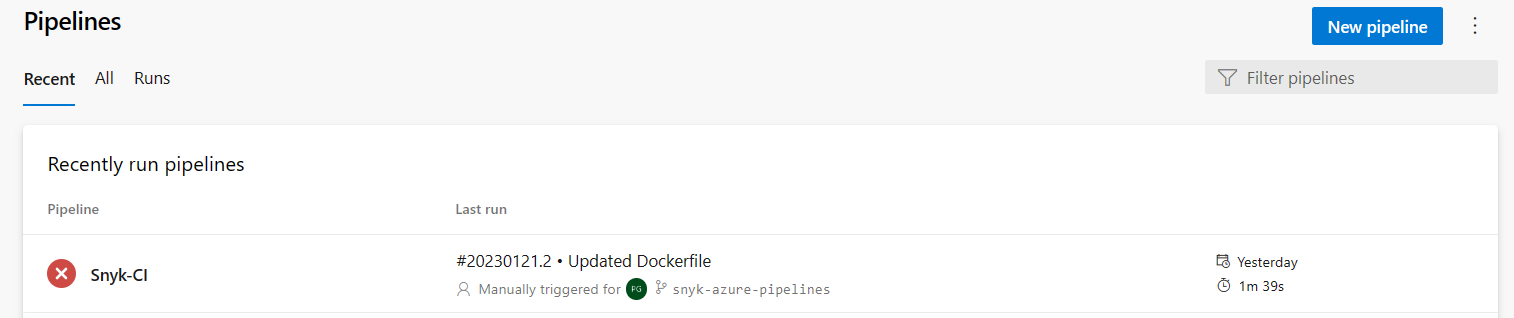
In the Runs tab, select a pipeline that has been run.
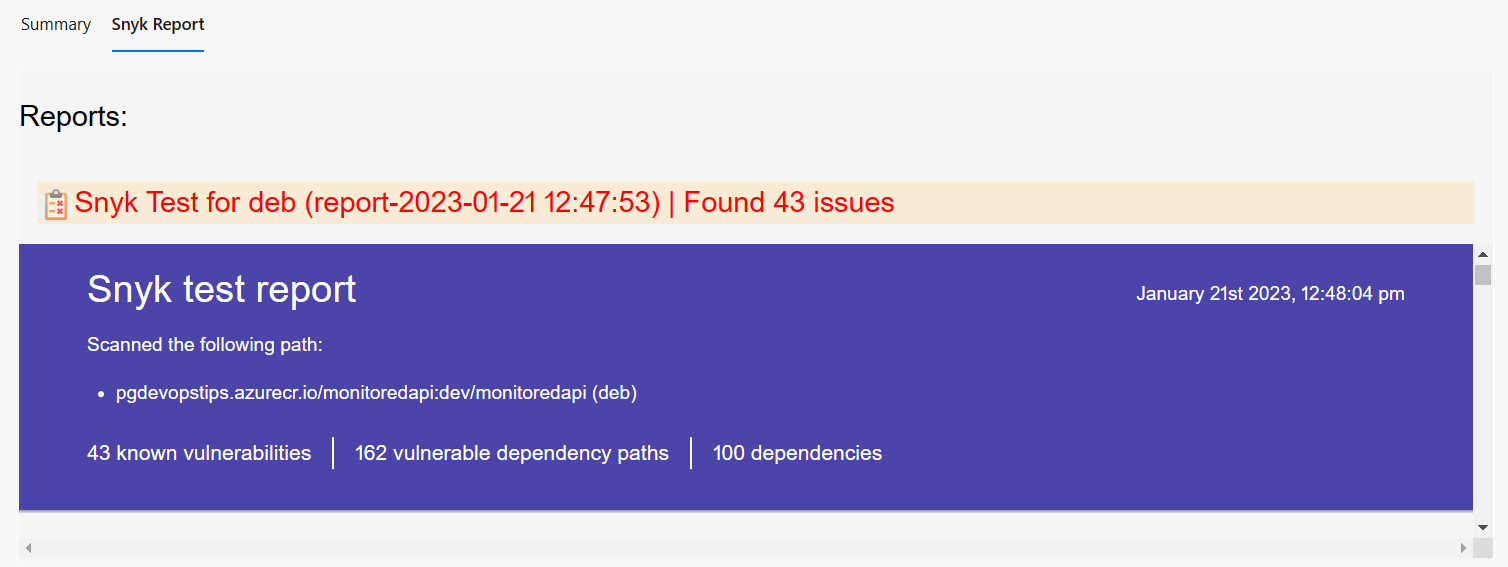
Select the Snyk Report tab to view the Snyk test report.
Got a comment?
All my articles are written and managed as Markdown files on GitHub.
Please add an issue or submit a pull request if something is not right on this article or you have a comment.
If you'd like to simply say "thanks", then please send me a so the rest of Twitter can see how awesome my work is.