Securing Blazor WebAssembly Applications with Microsoft Threat Modeling using STRIDE in Azure Ecosystem
Thursday, February 1, 2024
Securing Blazor WebAssembly Applications with Microsoft Threat Modeling using STRIDE in Azure Ecosystem
#azure-functions #azure-storage #blazor-webassembly #github-pages #github-webhook #microsoft-threat-modeling-tool #security #stride
This article is published at GitHub.You can raise issues, create pull requests or even fork the content...its open source.
In the era of cloud computing and distributed applications, securing web applications is more critical than ever. Microsoft Threat Modeling, coupled with the STRIDE framework, provides an effective strategy to identify and mitigate potential security threats. This article focuses on applying these principles to securing a Blazor WebAssembly application hosted on GitHub Pages in combination with a GitHub webhook connected to an Azure Function, which, in turn, communicates with an Azure Storage account.
Prerequisites
The following prerequisites will be required to complete this tutorial:
- Microsoft Threat Modeling Tool. If you don't have Microsoft's Threat Modeling Tool installed, download Microsoft's Threat Modeling Tool for free before you begin.
- Azure Threat Modeling Template. Clone the Azure Threat Modeling Template before you begin.
Understanding the Architecture
Detailed in this section is the architecture and what needs identifying for each element to analyse potential threats. For an infographic see the Build a Model section.
Blazor WebAssembly Application
- A web application hosted on GitHub Pages which supports the development of interactive and responsive web applications using C# and .NET technologies.
- Identify the assets, entry points, and critical functionalities within the Blazor WebAssembly application.
Azure Functions
- A serverless compute service which allows developers to run event-triggered functions without the need for managing infrastructure.
- Identify the various Azure Functions associated with the application, including their triggers and inputs.
Azure Storage Account
- Azure Storage provides scalable and secure storage solutions for data, including blobs, tables, queues, and files.
- Identify the specific types of data stored in the Azure Storage account and assess their sensitivity.
GitHub WebHook
- GitHub webhooks allow for real-time communication between GitHub and external services, triggering events upon code changes.
- Identify the GitHub webhook's role in the architecture.
Applying Microsoft Threat Modeling using STRIDE
Build a Model
Open the Microsoft Threat Modeling Tool.
Choose the latest version of the Azure Threat Model Template (Azure Architecture) you cloned in the prerequisites and then select Create A Model.
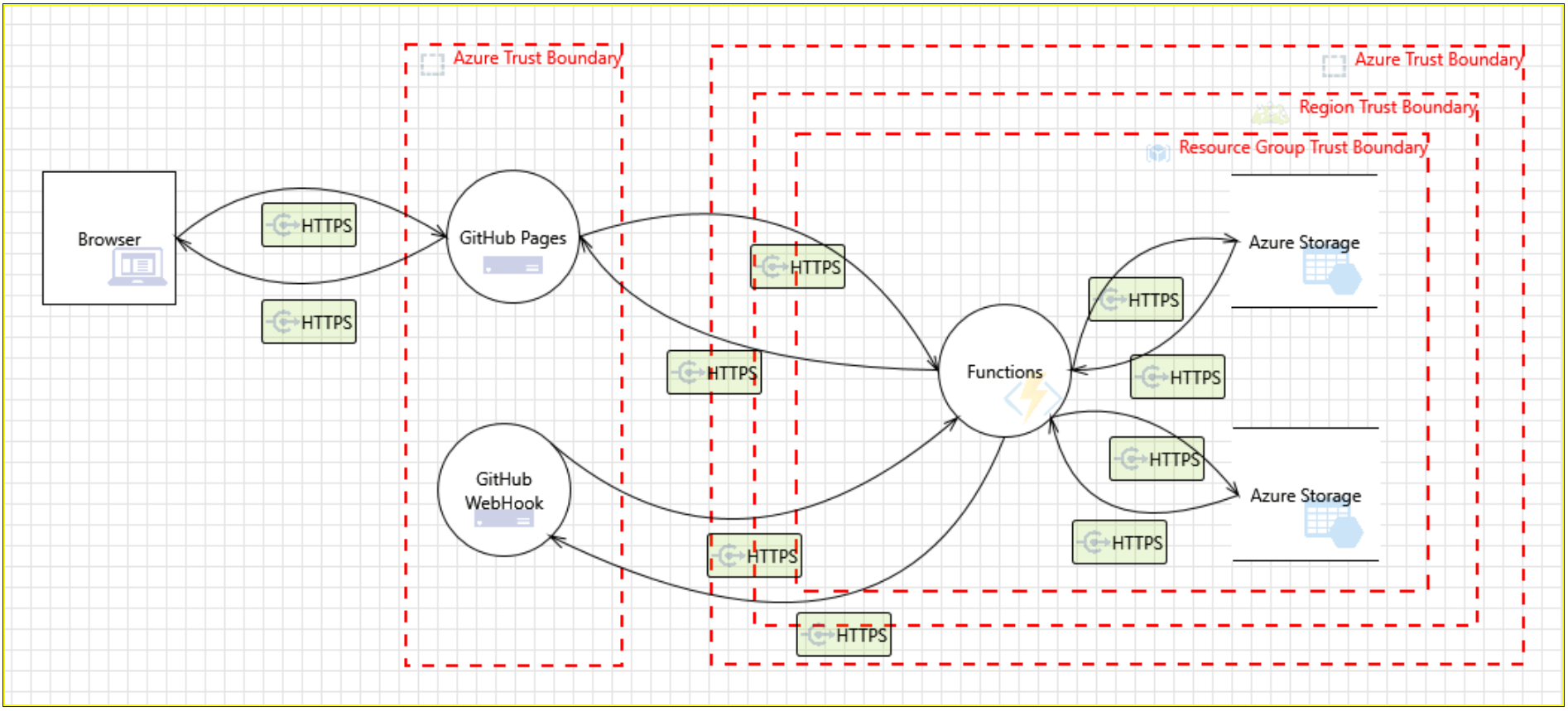
Drag and drop Elements from the Stencils onto the Canvas. This is the architecture detailed above.
Analysing Threats
To view a list of threats in a model, select View > Analysis View.
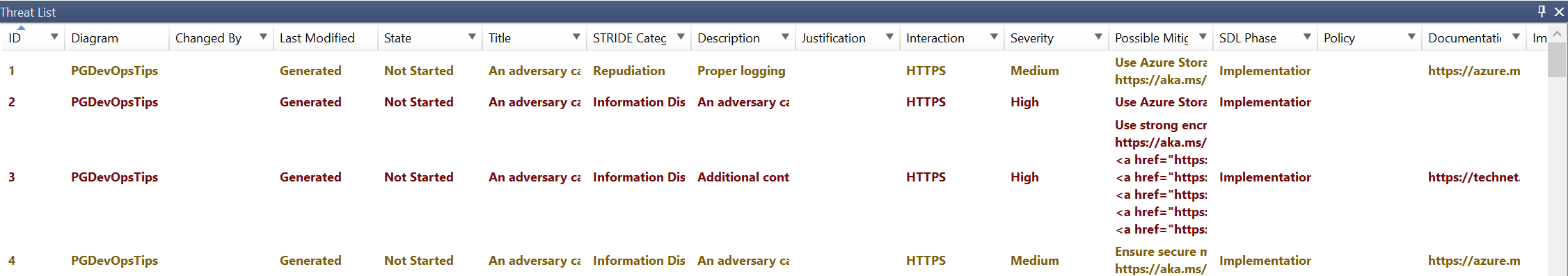
A Threat List will dock at the bottom of the application.
STRIDE framework
Detailed below is a description of each part of the STRIDE framework used by the Microsoft Threat Modeling Tool and how it applies to the architecture in this post.
Spoofing
- Identify potential spoofing threats, such as unauthorized access to the Blazor WebAssembly application, Azure Function or GitHub webhook.
- Implement strong authentication mechanisms, such as OAuth, for GitHub webhook integration, and leverage Microsoft Entra ID for securing access to the application and function.
Tampering
- Assess the possibility of code tampering within the Blazor WebAssembly application, the Azure Function, or the GitHub webhook.
- Utilise HTTPS to encrypt data in transit, employ code signing, and implement source code integrity checks to ensure the integrity of the application.
Repudiation
- Evaluate potential repudiation threats, such as users denying their actions in the Blazor WebAssembly application or GitHub events.
- Implement logging mechanisms within the application, Azure Function and GitHub webhook to track actions for auditing purposes.
Information Disclosure
- Identify points where sensitive information may be exposed, such as during data transmission or storage in the Azure Storage account.
- Implement encryption mechanisms, such as Azure Key Vault, to protect sensitive data at rest and in transit.
Denial of Service (DoS)
- Assess the vulnerability of the Blazor WebAssembly application, Azure Function and GitHub webhook to DoS attacks.
- Implement rate limiting, Azure CDN, and Azure DDoS Protection to mitigate potential denial of service threats.
Elevation of Privilege
- Examine the potential for attackers gaining unauthorized access or elevated privileges within the Blazor WebAssembly application, Azure Function or GitHub webhook.
- Implement the principle of least privilege, enforcing strict access controls, and regularly reviewing permissions.
Mitigating Threats
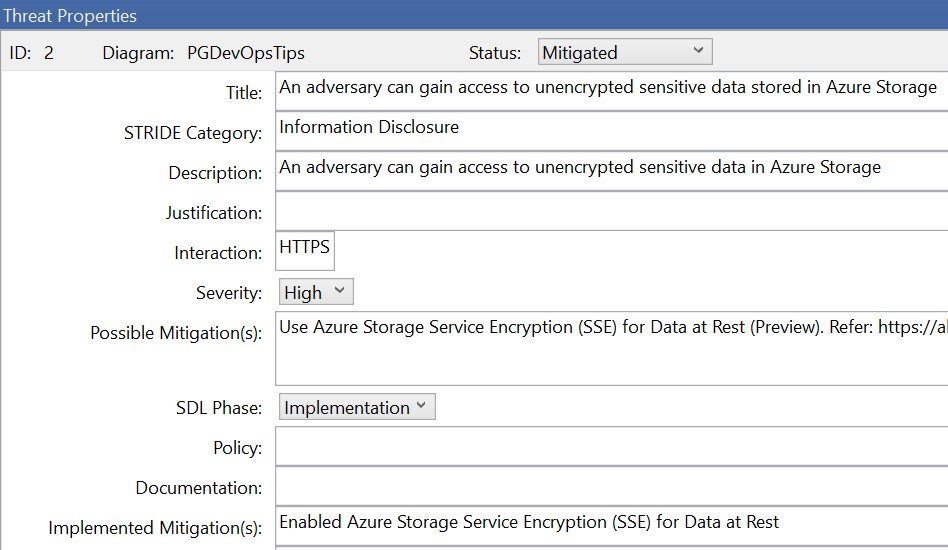
In the Threat list, select a Threat to open the threats properties.
Select a status of Mitigate in the drop down, and add a some information into the Implemented Mitigation(s) text area.
Mark Threats as Not Applicable
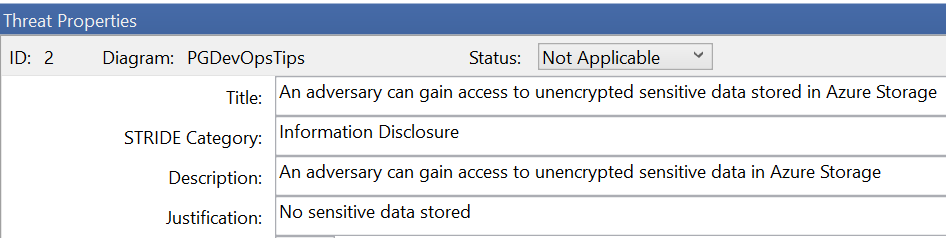
In the Threat list, select a Threat to open the threats properties.
Select a status of Not Applicable in the drop down, and add a some information into the Justification text box.
Generate a Report
To generate a Report which includes the model and a detailed breakdown of the threats, select Reports > Create Full Report.
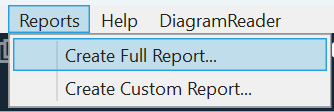
Save the Report and it will open in a browser.
Conclusion
Securing a comprehensive architecture that includes a Blazor WebAssembly application, Azure Function, Azure Storage, and GitHub webhook integration demands a meticulous approach to threat modeling. By systematically applying the STRIDE framework, developers can identify and address potential security risks at various levels of the application ecosystem. Incorporating best practices such as encryption, authentication, access controls, and continuous monitoring ensures a robust defense against threats, creating a resilient and secure end-to-end solution. Regularly updating threat models and staying informed about emerging security threats is crucial for maintaining the integrity and security of your integrated application.
Got a comment?
All my articles are written and managed as Markdown files on GitHub.
Please add an issue or submit a pull request if something is not right on this article or you have a comment.
If you'd like to simply say "thanks", then please send me a so the rest of Twitter can see how awesome my work is.